A few days ago I read a post by Mike Webster and was introduced to a product that peaked my interest.. (http://longwhiteclouds.com/2017/04/08/runecast-your-way-to-a-more-trouble-free-virtualization-environment/ ).
I have to spend time reviewing logs, dashboards, vCheck reports and other tools to keep virtual environments in a stable and healthy state. I have always wished there was a method to look at issues and match them up with VMware KB articles/data. I always want to be proactive and know of any potential issues or improvements to the configurations that I could do (before a customer would be impacted). I was like wow this is really cool to be ahead of issues as well as understand the issue/s.
I got time to install this and I have to say -- I am very wow'ed!!!!

What is Runecast?
Proactive tool that continuously checks your environment, vCenter, ESXi servers and VMs to ensure they are running at peak performance with no known configuration issues or security issues. IE --- > Proactively use VMware KBs, best practices and security hardening guidelines to protect your environment.
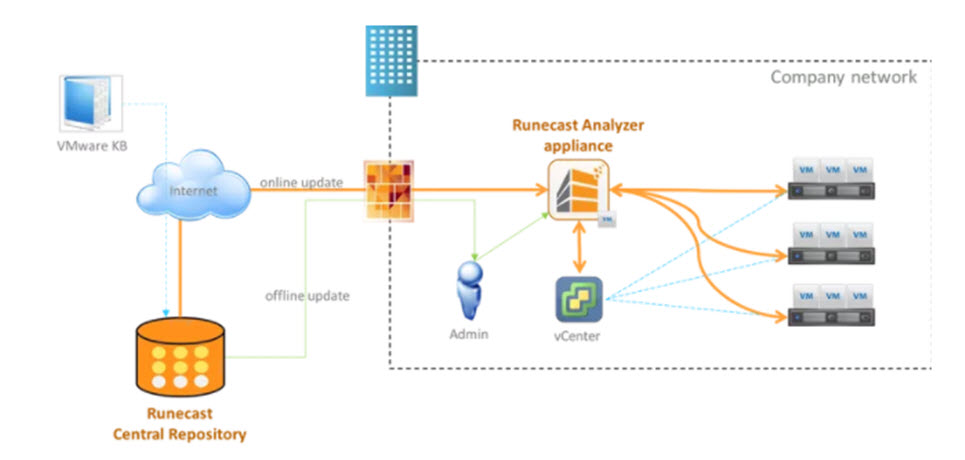
The really cool thing is you can stay up to date on industry issues that could impact your environment. Runcast is a virtual appliance (OVA) and can be updated from the internet or it can be updated via an ISO image (offline update). It is updated with information that has been mined from the VMware KBs and is used to proactively check log and configuration for issues in the virtual environment. It also has security configuration checks.
Installation
Installation was extremely simple, Runecast provides a virtual appliance (OVA) file that can be downloaded from the web and deployed via virtual center.
After configuring the VC permissions I clicked the “Analyze Now” button and the scan began. You can also schedule scans. I was also able to export findings. All good stuff.
Within a few minutes data started flowing into the dashboards and it found some known issues in the environment… my environment is rather large – many VCs, 100s+ hosts and over 1000s VMs, I also have a mix of versions – vSphere 6.x-5.x
I immediately started to check into the Best Practices area (dashboard) – seemed like the good place to start. As I soon found out I do have some critical known issues and configuration issues with in the environment – good work Runecast
Then I moved to the Issues List which is nice as it color codes issues in different categories (critical, major, Medium and low). I am not 100% sure how these are calculated but they do align with how I generally look at issues within an environment. I also notice some really cool info around PSODs and how it relates to hardware drivers and firmware updates.
I expanded to find some full details from and the KB article:
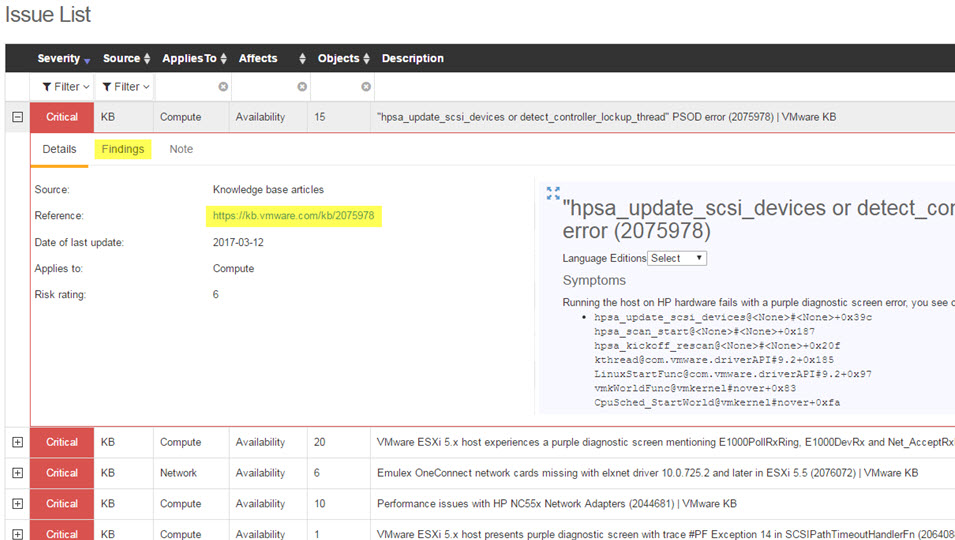
My environment will take some time to fix however with this view of issues/updates and the information in the KB, we could make the virtual environment a lot better in a proactive way. In a production environment this could save a lot of time so that issues are found faster and reported. We could actual enable an operation team to see the dashboards or via emails.
Security hardening is shown for my entire environment – for future discussion
Detailed log analysis is viewable – I didn’t get to this feature other than doing some searches so I’ll work on this more in the future.
Conclusion
Awesome Tool! I ran the app in my environment to try it out; it found reconfiguration issues, missed settings and missing patches. In an enterprise environment a human error and reconfiguration accounts for a large number of issues.
I would strongly recommend running an analysis to check your virtual environment to see if things are running at peak performance and how can it improve your proactive state for better stability.
Check it out: https://www.runecast.biz/
Runecast - few items would like to see updated or how-to docs:
I would like to understand the categories better
How to export the report with the findings
What is the plan to add other products into Runecast (IE other hypervisors/hardware vendors, etc...)